- ISO 27001 Certified Company
- +91 8660048488
- contact@levontechno.com
- Asia | Australia | Africa | America | Europe
- Launch
- Enterprise
- Value services
- Website Development
- Ecommerce Solutions
- Mobile App Solutions
- Enterprise Development
- Business Marketing
- Support & Maintenance
- Website development
- Ecommerce Development
- Mobile app development
Together, We Create Extraordinary Solutions
- Offerings
- Customized Softwares
- ERP Software
- HRM Software
- CRM Software
- Chatbot System
- Ticketing Software
- Task Management
- Products
- Support & Maintaince
- Startup Business Suite ( Graphics designing, GMB, Emails)
- Security Maintenance
- Compliance and Upgrades
- Backup & Recovery
- Monitoring & Analytics
- Social Media Management
- Revamp Management
Together, We Create Extraordinary Solutions
- Network
- Bangladesh
- Bhutan
- Cambodia
- China
- India
- Indonesia
- Japan
- Malaysia
- kazakhstan
- North Korea
- South Korea
- Kyrgyzstan
- Laos
- Malaysia
- Maldives
- Mongolia
- Myanmar
- Nepal
- Philippines
- Singapore
- Sri Lanka
- Taiwan
- Tajikistan
- Thailand
- Thailand
- Turkmenistan
- Uzbekistan
- Vietnam
- Australia
- East Timor
- Fiji
- Kiribati
- Marshall Islands
- Nauru
- New Zealand
- Palau
- Papua New Guinea
- Samoa
- Solomon Islands
- Tonga
- Tuvalu
- Vanuatu
- Angola
- Benin
- Botswana
- Burkina Faso
- Burundi
- Cameroon
- Cape Verde
- Equatorial Guinea
- Eritrea
- Ethiopia
- Gabon
- The Gambia
- Ghana
- Guinea
- Guinea-Bissau
- Kenya
- Lesotho
- Liberia
- Madagascar
- Malawi
- Mali
- Mauritania
- Mauritius
- Mozambique
- Namibia
- Niger
- Nigeria
- Rwanda
- Sao Tome and Principe
- Senegal
- Seychelles
- Sierra Leone
- South Africa
- South Sudan
- Sudan
- Swaziland
- Tanzania
- Togo
- Uganda
- Zambia
- Zimbabwe
- Albania
- Andorra
- Armenia
- Austria
- Belarus
- Belgium
- Bosnia and Herzegovina
- Bulgaria
- Croatia
- Cyprus
- Czech Republic
- Denmark
- Estonia
- Finland
- France
- Georgia
- Germany
- Greece
- Hungary
- Iceland
- Ireland
- Italy
- Kosovo
- Latvia
- Liechtenstein
- Lithuania
- Luxembourg
- Macedonia
- Malta
- Moldova
- Monaco
- Montenegro
- Netherlands
- Norway
- Poland
- Portugal
- Romania
- Russia
- San Marino
- Serbia
- Slovakia
- Slovenia
- Spain
- Sweden
- Switzerland
- Ukraine
- Vatican City
- United Kingdom
- Afghanistan
- Algeria
- Azerbaijan
- Bahrain
- Egypt
- Iran
- Iraq
- Israel
- Jordan
- Kuwait
- Lebanon
- Libya
- Morocco
- Oman
- Qatar
- Saudi Arabia
- Somalia
- Syria
- Tunisia
- Turkey
- United Arab Emirates
- Yemen
- Canada
- Greenland
- Mexico
- The United States of America
- Antigua and Barbuda
- The Bahamas
- Barbados
- Belize
- Costa Rica
- Cuba
- Dominica
- Dominican Republic
- El Salvador
- Grenada
- Guatemala
- Haiti
- Honduras
- Jamaica
- Nicaragua
- Panama
- Saint Kitts and Nevis
- Saint Lucia
- Saint Vincent and the Grenadines
- Trinidad and Tobago
- Argentina
- Bolivia
- Brazil
- Chile
- Colombia
- Ecuador
- Guyana
- Paraguay
- Peru
- Suriname
- Uruguay
- Venezuela
Together, We Create Extraordinary Solutions
- Connect
- Launch
- Enterprise
- Value services
- Website Development
- Ecommerce Solutions
- Mobile App Solutions
- Enterprise Development
- Business Marketing
- Support & Maintenance
- Website development
- Ecommerce Development
- Mobile app development
Together, We Create Extraordinary Solutions
- Offerings
- Customized Softwares
- ERP Software
- HRM Software
- CRM Software
- Chatbot System
- Ticketing Software
- Task Management
- Products
- Support & Maintaince
- Startup Business Suite ( Graphics designing, GMB, Emails)
- Security Maintenance
- Compliance and Upgrades
- Backup & Recovery
- Monitoring & Analytics
- Social Media Management
- Revamp Management
Together, We Create Extraordinary Solutions
- Network
- Bangladesh
- Bhutan
- Cambodia
- China
- India
- Indonesia
- Japan
- Malaysia
- kazakhstan
- North Korea
- South Korea
- Kyrgyzstan
- Laos
- Malaysia
- Maldives
- Mongolia
- Myanmar
- Nepal
- Philippines
- Singapore
- Sri Lanka
- Taiwan
- Tajikistan
- Thailand
- Thailand
- Turkmenistan
- Uzbekistan
- Vietnam
- Australia
- East Timor
- Fiji
- Kiribati
- Marshall Islands
- Nauru
- New Zealand
- Palau
- Papua New Guinea
- Samoa
- Solomon Islands
- Tonga
- Tuvalu
- Vanuatu
- Angola
- Benin
- Botswana
- Burkina Faso
- Burundi
- Cameroon
- Cape Verde
- Equatorial Guinea
- Eritrea
- Ethiopia
- Gabon
- The Gambia
- Ghana
- Guinea
- Guinea-Bissau
- Kenya
- Lesotho
- Liberia
- Madagascar
- Malawi
- Mali
- Mauritania
- Mauritius
- Mozambique
- Namibia
- Niger
- Nigeria
- Rwanda
- Sao Tome and Principe
- Senegal
- Seychelles
- Sierra Leone
- South Africa
- South Sudan
- Sudan
- Swaziland
- Tanzania
- Togo
- Uganda
- Zambia
- Zimbabwe
- Albania
- Andorra
- Armenia
- Austria
- Belarus
- Belgium
- Bosnia and Herzegovina
- Bulgaria
- Croatia
- Cyprus
- Czech Republic
- Denmark
- Estonia
- Finland
- France
- Georgia
- Germany
- Greece
- Hungary
- Iceland
- Ireland
- Italy
- Kosovo
- Latvia
- Liechtenstein
- Lithuania
- Luxembourg
- Macedonia
- Malta
- Moldova
- Monaco
- Montenegro
- Netherlands
- Norway
- Poland
- Portugal
- Romania
- Russia
- San Marino
- Serbia
- Slovakia
- Slovenia
- Spain
- Sweden
- Switzerland
- Ukraine
- Vatican City
- United Kingdom
- Afghanistan
- Algeria
- Azerbaijan
- Bahrain
- Egypt
- Iran
- Iraq
- Israel
- Jordan
- Kuwait
- Lebanon
- Libya
- Morocco
- Oman
- Qatar
- Saudi Arabia
- Somalia
- Syria
- Tunisia
- Turkey
- United Arab Emirates
- Yemen
- Canada
- Greenland
- Mexico
- The United States of America
- Antigua and Barbuda
- The Bahamas
- Barbados
- Belize
- Costa Rica
- Cuba
- Dominica
- Dominican Republic
- El Salvador
- Grenada
- Guatemala
- Haiti
- Honduras
- Jamaica
- Nicaragua
- Panama
- Saint Kitts and Nevis
- Saint Lucia
- Saint Vincent and the Grenadines
- Trinidad and Tobago
- Argentina
- Bolivia
- Brazil
- Chile
- Colombia
- Ecuador
- Guyana
- Paraguay
- Peru
- Suriname
- Uruguay
- Venezuela
Together, We Create Extraordinary Solutions
- Connect
Office Address
Asia | Australia | Africa | Middle East | America | Europe |
Phone Number
Email Address
- Launch
- Enterprise
- Value services
- Website Development
- Ecommerce Solutions
- Mobile App Solutions
- Enterprise Development
- Business Marketing
- Support & Maintenance
- Website development
- Ecommerce Development
- Mobile app development
Together, We Create Extraordinary Solutions
- Offerings
- Customized Softwares
- ERP Software
- HRM Software
- CRM Software
- Chatbot System
- Ticketing Software
- Task Management
- Products
- Support & Maintaince
- Startup Business Suite ( Graphics designing, GMB, Emails)
- Security Maintenance
- Compliance and Upgrades
- Backup & Recovery
- Monitoring & Analytics
- Social Media Management
- Revamp Management
Together, We Create Extraordinary Solutions
- Network
- Bangladesh
- Bhutan
- Cambodia
- China
- India
- Indonesia
- Japan
- Malaysia
- kazakhstan
- North Korea
- South Korea
- Kyrgyzstan
- Laos
- Malaysia
- Maldives
- Mongolia
- Myanmar
- Nepal
- Philippines
- Singapore
- Sri Lanka
- Taiwan
- Tajikistan
- Thailand
- Thailand
- Turkmenistan
- Uzbekistan
- Vietnam
- Australia
- East Timor
- Fiji
- Kiribati
- Marshall Islands
- Nauru
- New Zealand
- Palau
- Papua New Guinea
- Samoa
- Solomon Islands
- Tonga
- Tuvalu
- Vanuatu
- Angola
- Benin
- Botswana
- Burkina Faso
- Burundi
- Cameroon
- Cape Verde
- Equatorial Guinea
- Eritrea
- Ethiopia
- Gabon
- The Gambia
- Ghana
- Guinea
- Guinea-Bissau
- Kenya
- Lesotho
- Liberia
- Madagascar
- Malawi
- Mali
- Mauritania
- Mauritius
- Mozambique
- Namibia
- Niger
- Nigeria
- Rwanda
- Sao Tome and Principe
- Senegal
- Seychelles
- Sierra Leone
- South Africa
- South Sudan
- Sudan
- Swaziland
- Tanzania
- Togo
- Uganda
- Zambia
- Zimbabwe
- Albania
- Andorra
- Armenia
- Austria
- Belarus
- Belgium
- Bosnia and Herzegovina
- Bulgaria
- Croatia
- Cyprus
- Czech Republic
- Denmark
- Estonia
- Finland
- France
- Georgia
- Germany
- Greece
- Hungary
- Iceland
- Ireland
- Italy
- Kosovo
- Latvia
- Liechtenstein
- Lithuania
- Luxembourg
- Macedonia
- Malta
- Moldova
- Monaco
- Montenegro
- Netherlands
- Norway
- Poland
- Portugal
- Romania
- Russia
- San Marino
- Serbia
- Slovakia
- Slovenia
- Spain
- Sweden
- Switzerland
- Ukraine
- Vatican City
- United Kingdom
- Afghanistan
- Algeria
- Azerbaijan
- Bahrain
- Egypt
- Iran
- Iraq
- Israel
- Jordan
- Kuwait
- Lebanon
- Libya
- Morocco
- Oman
- Qatar
- Saudi Arabia
- Somalia
- Syria
- Tunisia
- Turkey
- United Arab Emirates
- Yemen
- Canada
- Greenland
- Mexico
- The United States of America
- Antigua and Barbuda
- The Bahamas
- Barbados
- Belize
- Costa Rica
- Cuba
- Dominica
- Dominican Republic
- El Salvador
- Grenada
- Guatemala
- Haiti
- Honduras
- Jamaica
- Nicaragua
- Panama
- Saint Kitts and Nevis
- Saint Lucia
- Saint Vincent and the Grenadines
- Trinidad and Tobago
- Argentina
- Bolivia
- Brazil
- Chile
- Colombia
- Ecuador
- Guyana
- Paraguay
- Peru
- Suriname
- Uruguay
- Venezuela
Together, We Create Extraordinary Solutions
- Connect
- Launch
- Enterprise
- Value services
- Website Development
- Ecommerce Solutions
- Mobile App Solutions
- Enterprise Development
- Business Marketing
- Support & Maintenance
- Website development
- Ecommerce Development
- Mobile app development
Together, We Create Extraordinary Solutions
- Offerings
- Customized Softwares
- ERP Software
- HRM Software
- CRM Software
- Chatbot System
- Ticketing Software
- Task Management
- Products
- Support & Maintaince
- Startup Business Suite ( Graphics designing, GMB, Emails)
- Security Maintenance
- Compliance and Upgrades
- Backup & Recovery
- Monitoring & Analytics
- Social Media Management
- Revamp Management
Together, We Create Extraordinary Solutions
- Network
- Bangladesh
- Bhutan
- Cambodia
- China
- India
- Indonesia
- Japan
- Malaysia
- kazakhstan
- North Korea
- South Korea
- Kyrgyzstan
- Laos
- Malaysia
- Maldives
- Mongolia
- Myanmar
- Nepal
- Philippines
- Singapore
- Sri Lanka
- Taiwan
- Tajikistan
- Thailand
- Thailand
- Turkmenistan
- Uzbekistan
- Vietnam
- Australia
- East Timor
- Fiji
- Kiribati
- Marshall Islands
- Nauru
- New Zealand
- Palau
- Papua New Guinea
- Samoa
- Solomon Islands
- Tonga
- Tuvalu
- Vanuatu
- Angola
- Benin
- Botswana
- Burkina Faso
- Burundi
- Cameroon
- Cape Verde
- Equatorial Guinea
- Eritrea
- Ethiopia
- Gabon
- The Gambia
- Ghana
- Guinea
- Guinea-Bissau
- Kenya
- Lesotho
- Liberia
- Madagascar
- Malawi
- Mali
- Mauritania
- Mauritius
- Mozambique
- Namibia
- Niger
- Nigeria
- Rwanda
- Sao Tome and Principe
- Senegal
- Seychelles
- Sierra Leone
- South Africa
- South Sudan
- Sudan
- Swaziland
- Tanzania
- Togo
- Uganda
- Zambia
- Zimbabwe
- Albania
- Andorra
- Armenia
- Austria
- Belarus
- Belgium
- Bosnia and Herzegovina
- Bulgaria
- Croatia
- Cyprus
- Czech Republic
- Denmark
- Estonia
- Finland
- France
- Georgia
- Germany
- Greece
- Hungary
- Iceland
- Ireland
- Italy
- Kosovo
- Latvia
- Liechtenstein
- Lithuania
- Luxembourg
- Macedonia
- Malta
- Moldova
- Monaco
- Montenegro
- Netherlands
- Norway
- Poland
- Portugal
- Romania
- Russia
- San Marino
- Serbia
- Slovakia
- Slovenia
- Spain
- Sweden
- Switzerland
- Ukraine
- Vatican City
- United Kingdom
- Afghanistan
- Algeria
- Azerbaijan
- Bahrain
- Egypt
- Iran
- Iraq
- Israel
- Jordan
- Kuwait
- Lebanon
- Libya
- Morocco
- Oman
- Qatar
- Saudi Arabia
- Somalia
- Syria
- Tunisia
- Turkey
- United Arab Emirates
- Yemen
- Canada
- Greenland
- Mexico
- The United States of America
- Antigua and Barbuda
- The Bahamas
- Barbados
- Belize
- Costa Rica
- Cuba
- Dominica
- Dominican Republic
- El Salvador
- Grenada
- Guatemala
- Haiti
- Honduras
- Jamaica
- Nicaragua
- Panama
- Saint Kitts and Nevis
- Saint Lucia
- Saint Vincent and the Grenadines
- Trinidad and Tobago
- Argentina
- Bolivia
- Brazil
- Chile
- Colombia
- Ecuador
- Guyana
- Paraguay
- Peru
- Suriname
- Uruguay
- Venezuela
Together, We Create Extraordinary Solutions
- Connect
Office Address
Asia | Australia | Africa | Middle East | America | Europe |
Phone Number
Email Address
Cybersecurity Services
Protecting Your Digital Assets with Comprehensive Security Solutions
Introduction
Cybersecurity services are designed to protect organizations from a wide range of cyber threats, ensuring the security of digital assets, sensitive information, and IT infrastructure. These services encompass proactive measures, monitoring, and response strategies to mitigate risks associated with data breaches, hacking, malware, and other cyberattacks.
- Vulnerability Assessments and Penetration Testing: Identifying and addressing security weaknesses in your systems and networks.
- Threat Detection and Incident Response: Real-time monitoring and rapid response to potential cyber threats.
- Data Protection and Encryption: Safeguarding sensitive data both at rest and in transit.
- Network Security: Implementing firewalls, intrusion detection systems, and secure network architecture to prevent unauthorized access.
- Endpoint Protection: Securing devices like computers, mobile phones, and IoT devices from potential threats.
Key Benefits of Cybersecurity Services
1. Protection from Cyber Threats
Cybersecurity services safeguard businesses from a wide array of cyberattacks, including malware, ransomware, phishing, and data breaches, ensuring the security of sensitive information and IT infrastructure.
2. Data Security and Integrity
Effective cybersecurity measures help protect critical business data from unauthorized access, theft, or damage. This ensures data confidentiality, integrity, and availability, especially for sensitive customer information.
3. Risk Management and Mitigation
These services assess vulnerabilities in systems, identify potential risks, and implement measures to mitigate them. This proactive approach reduces the likelihood of financial losses, legal issues, and reputational damage.
4. Compliance with Regulations
Cybersecurity services help businesses stay compliant with various regulatory frameworks and industry standards, such as GDPR, HIPAA, PCI-DSS, and CCPA. Adherence to these regulations avoids penalties and fosters trust among stakeholders.
5. Real-Time Threat Detection and Response
Continuous monitoring and advanced threat detection capabilities allow businesses to identify and respond to cyber threats in real time, minimizing the impact of potential security breaches.
6. Business Continuity and Disaster Recovery
Cybersecurity services ensure that robust backup and disaster recovery strategies are in place, enabling businesses to recover quickly from cyberattacks, natural disasters, or system failures without significant operational disruption.
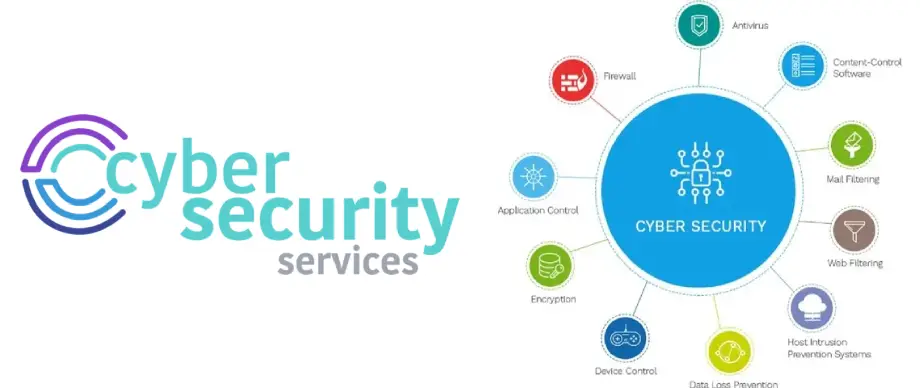
Cybersecurity Services We Provide :
Vulnerability Assessments and Penetration Testing (VAPT)
- Identify potential weaknesses in your IT systems and applications through comprehensive testing, and address vulnerabilities before cybercriminals exploit them.
Managed Security Services
- 24/7 monitoring and management of your security infrastructure, including firewalls, intrusion detection/prevention systems (IDS/IPS), and security information and event management (SIEM).
Threat Detection and Incident Response
- Real-time detection and analysis of cyber threats with rapid incident response to mitigate damage and minimize downtime in the event of a cyberattack.
Network Security
- Implement and manage firewalls, secure VPNs, and network segmentation to protect your network from external threats and unauthorized access.
Endpoint Security
- Protect your business’s devices, such as laptops, mobile phones, and servers, with advanced antivirus, anti-malware, and device management solutions to prevent security breaches.
Our Cybersecurity Services Process
Consultation:
We begin by understanding your project requirements and business goals
Planning:
Drafting a comprehensive architecture and timeline tailored to your project.
Design
Crafting an intuitive and engaging front-end experience using Cybersecurity
Development:
Building and rigorously testing your Cybersecurity application for optimal performance
Deployment:
Launching your application with real-time support and continuous monitoring.
At Levon Techno Solutions, our dedicated team of Cybersecurity developers excels in full-stack development, delivering high-performance applications tailored to your needs. We prioritize seamless user experiences and utilize a range of technology stacks that blend the best tools and frameworks.
Comprehensive Full-Stack Approach
Leverage our expertise across both front-end and back-end technologies for a cohesive development process.
Streamlined Starter Architecture
Kickstart your project with our well-researched starter architecture, designed to save development time and resources.
Optimized Performance
Enjoy applications that are fast and responsive, ensuring an exceptional user experience at every interaction.
Technologies We Use & Work With
At Levon Techno Solutions, we utilize a comprehensive tech stack to deliver exceptional Wix applications. Our expertise includes:
Ready to Start Your Cybersecurity Project?
Partner with Levon Techno Solutions, the best Cybersecurity website development company, to bring your web application to life. Reach out today to learn more about how our Cybersecurity expertise can transform your business.

Frequently Asked Questions
Clearing Doubts, Providing Clarity, and Empowering Informed Decisions
Cybersecurity services involve a range of solutions and strategies to protect businesses from cyber threats. These services include vulnerability assessments, threat detection, incident response, data protection, network security, and more to safeguard digital assets and IT systems from attacks like hacking, malware, phishing, and ransomware.
The most common cyber threats include:
- Phishing: Fraudulent attempts to obtain sensitive information.
- Malware: Malicious software designed to harm or exploit devices.
- Ransomware: A type of malware that locks data and demands ransom for access.
- DDoS Attacks: Distributed Denial-of-Service attacks that disrupt services by overwhelming systems.
- Insider Threats: Security breaches caused by employees or authorized individuals.
Managed Security Services (MSS) are outsourced solutions where a third-party provider monitors and manages your cybersecurity infrastructure 24/7. This includes monitoring for threats, responding to incidents, and maintaining firewalls, anti-virus systems, and SIEM (Security Information and Event Management) tools.
Cybersecurity services include disaster recovery planning, ensuring that in the event of a cyberattack or other catastrophic event, your business can recover quickly. This involves backing up critical data, maintaining redundancy in systems, and having a structured recovery process to minimize downtime and data loss.
Encryption is the process of converting sensitive data into a code to prevent unauthorized access. It is used to protect data both at rest (stored data) and in transit (data being transferred), ensuring that even if cybercriminals intercept the data, they cannot read or use it without the decryption key.
Cybersecurity measures should be continuously updated to keep pace with evolving threats. Regular security assessments, software updates, and patch management are critical to maintaining the security of your systems and data.
- Malware is a general term for malicious software designed to damage, disrupt, or gain unauthorized access to systems.
- Ransomware is a specific type of malware that encrypts a victim’s data and demands payment (ransom) to restore access.
The cost of cybersecurity services varies based on the size of your business, the complexity of your IT environment, and the level of protection required. Services can range from basic security packages to comprehensive, fully managed security solutions.
